Cloud Security is
Now a Conversation
Your AI-Powered Cloud Assistant to Build, Secure, and Operate your cloud environment.
1,700+
Customizable Configuration
Templates
2,400+
Customer Security
Assessments Yearly
70%
Faster Well-Architected
Reviews
<15 Min
Security Assessment
Results
BUILT-IN AI
AI Assistance by Your Side
Finally, an AI tool that does more than just tell you what to do
Ditch scripts and generate any CloudFormation template
Identify potential security risks
Have real-time visibility into resource usage
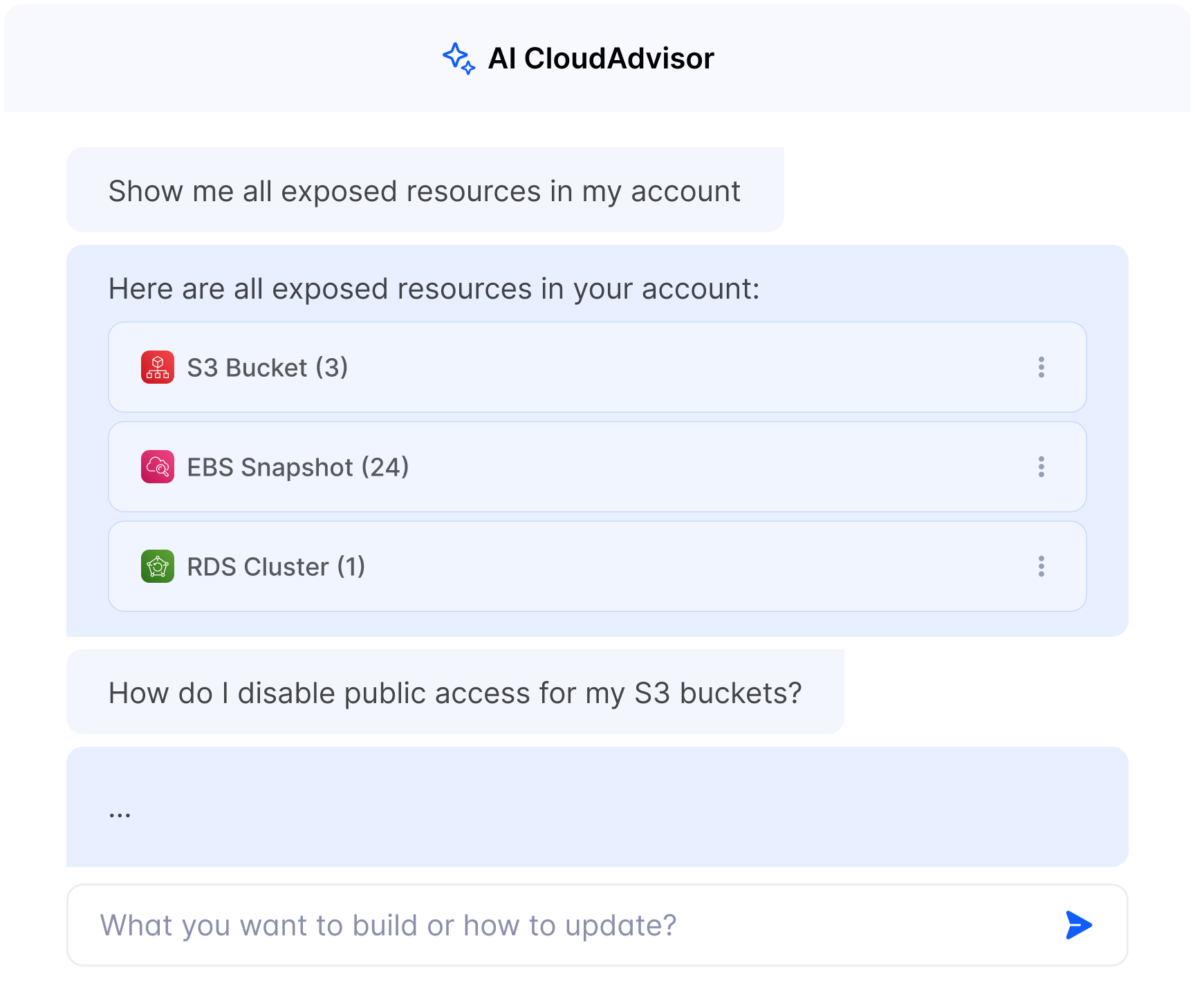
You can ask it "Show me all exposed resources in my account"
or "Create an end-to-end backup strategy for my account"
or "Create an end-to-end backup strategy for my account"
BUILD IN MINUTES
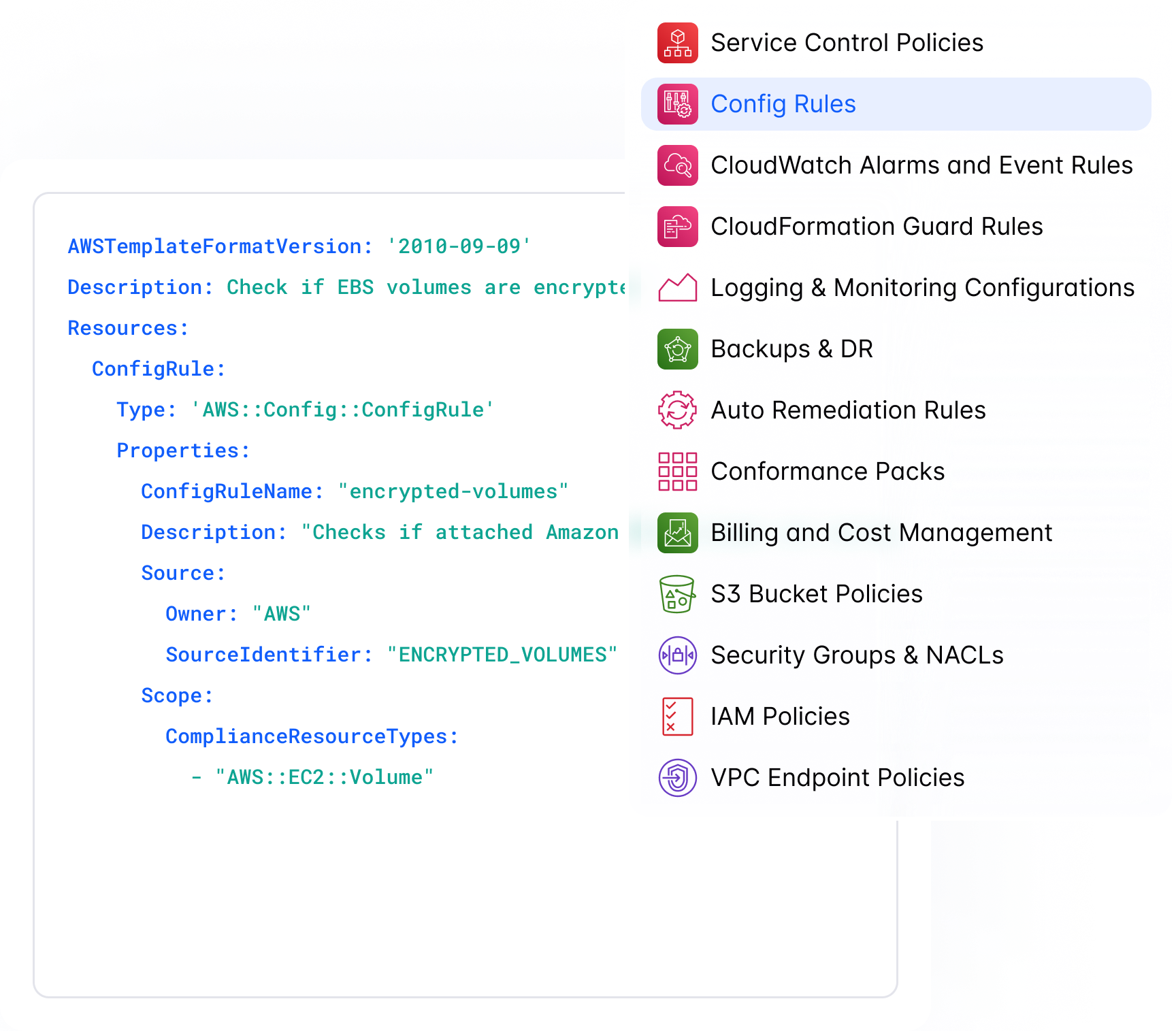
Infrastructure-As-Code Made Easy
With 1,000's of pre-made build and configuration presets you never have to start from scratch again.
Build Infrastructure-as-code templates with ease
Identify potential security risks
Save your custom templates for re-use
Share templates with teammates and/or clients
Create your own templates with AI assistance by simply describing the environment you want to deploy.
SECURITY & COMPLIANCE
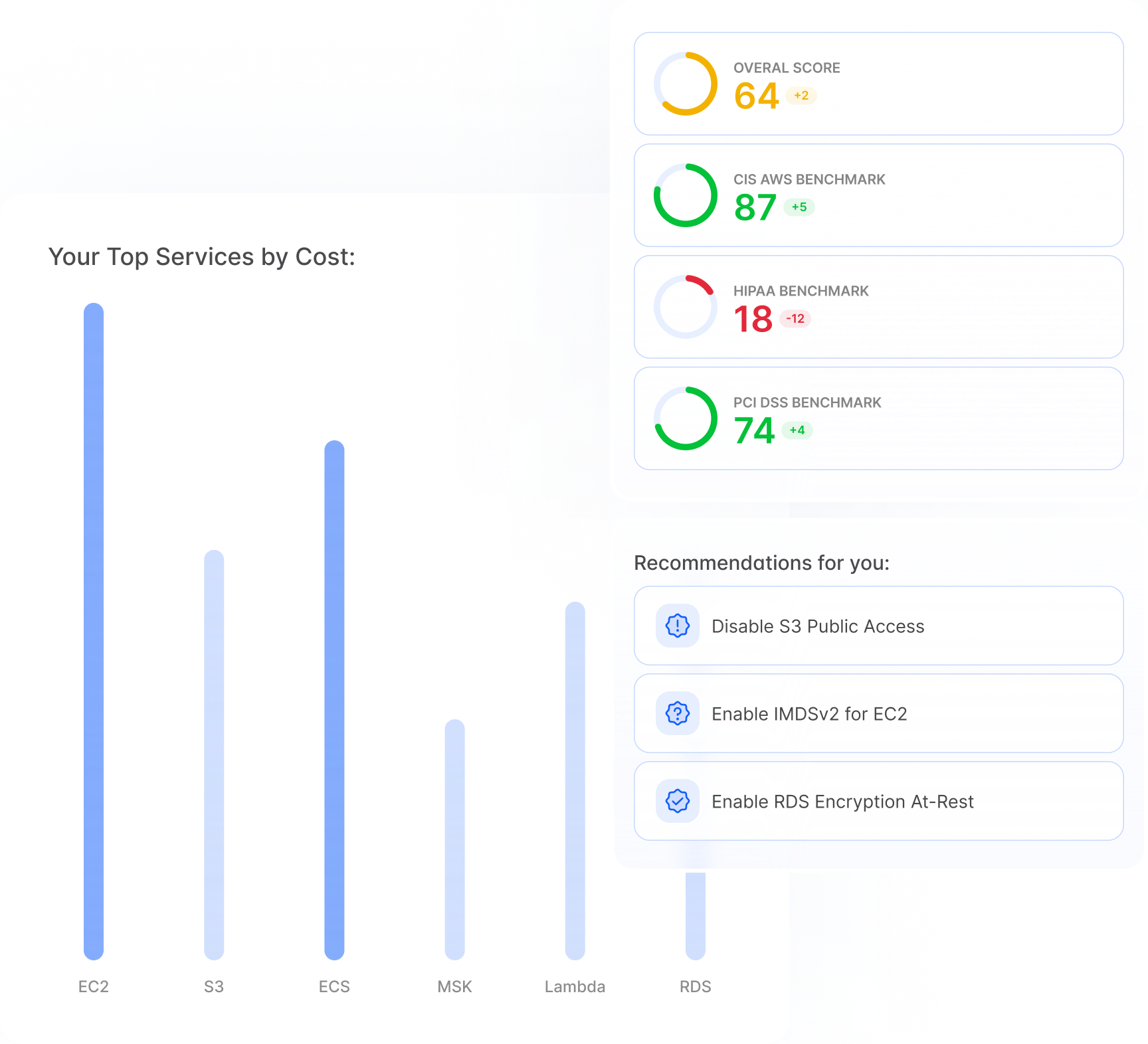
Simplified Compliance
Spend less time on manual security checks and more time addressing vulnerabilities.
One-click Remediation Templates
Automated email summaries
Simplified Compliance
Ensure you remain compliant with 15+ compliance reports that are guaranteed to be up-to-date, and easily share your progress over time with your auditor.
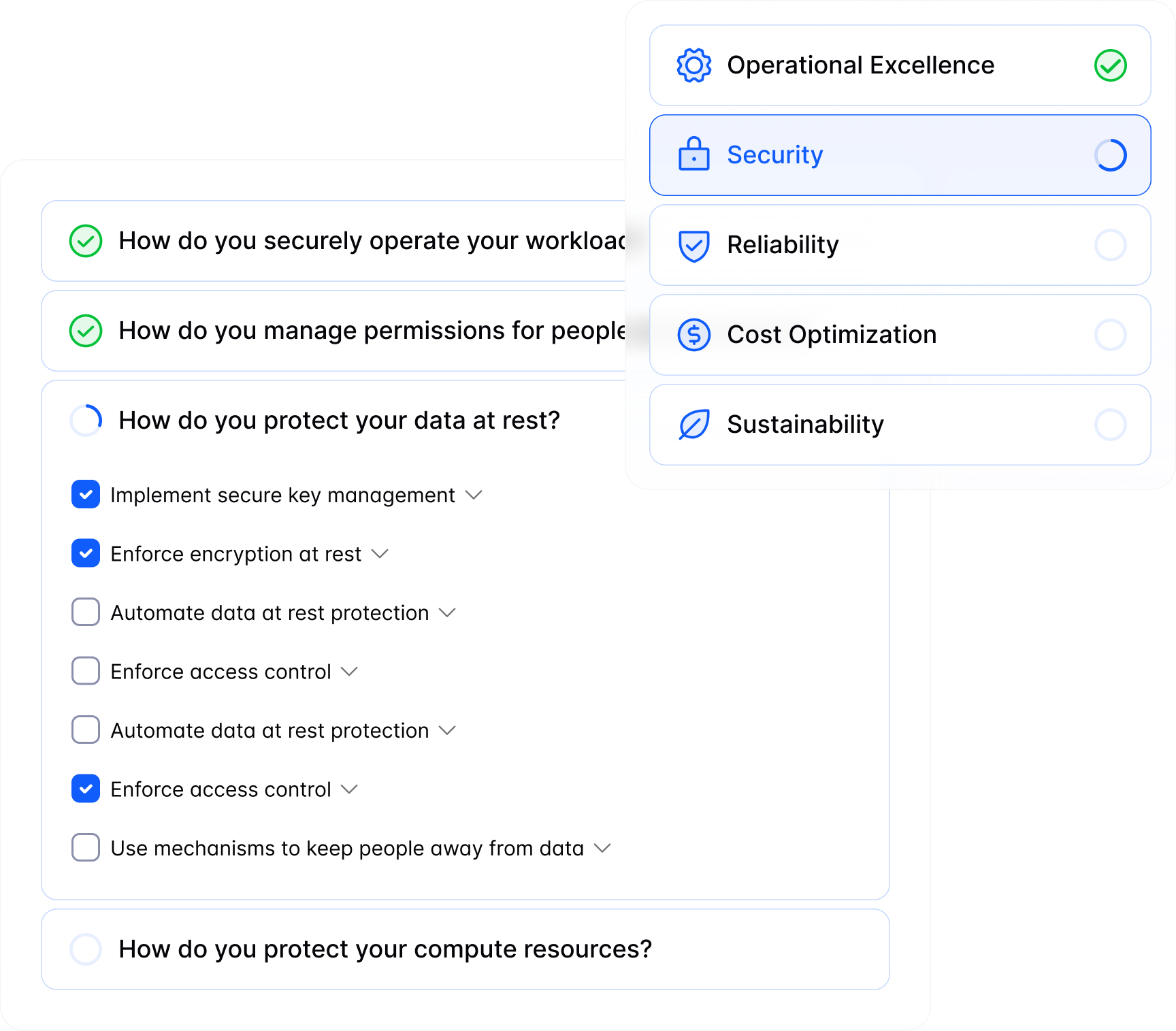
AWS WELL-ARCHITECTED
Well-Architected Reviews, Automated
Immediately upon completion of the account evaluation you will be provided with a list of suggested answers for your AWS Well-Architected review.
Now you can breeze through the review
Eliminate HRIs faster to claim credits for your clients
Get back to implementing best practices.
Simply accept our suggestions or collaborate with CloudAdvisor to complete the questionnaire.
Managed Services Reinvented
Bringing it All Together for MSPs
The future of manged cloud services is AI-powered insights, automation and collaboration.Now you can provide your customers with role-based access to reports, configurations, and audits.
With automated policy enforcement, threat detection, and analysis you'll become a one-stop-shop for all your client's cloud needs.