You must be logged in to view saved presets
Guided Walkthroughs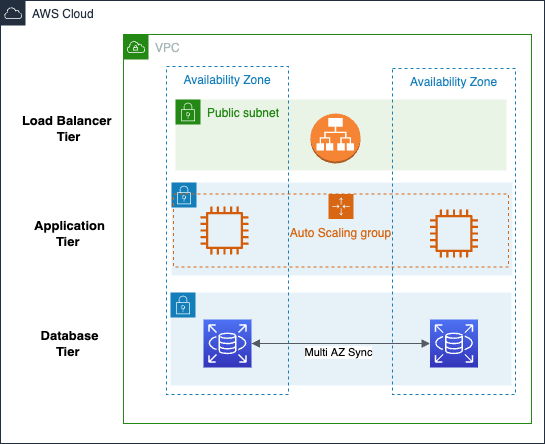
Classic Three Tier Application

Overview
This guided walkthrough sets up a common 3-tier web application infrastructure in your AWS account, including:
- AWS VPC setup including different subnet tier options and internet access settings (or reference an existing VPC)
- Load Balancer configuration including listening ports, SSL certificates, etc.
- Application Instances: EC2 instance configuration and optional Auto Scaling groups
- Database to optionally add an Amazon RDS instance or cluster with options to customize the configuration including Multi-AZ, engine, etc.
A premium subscription is required for this content
Deploy
Classic Three Tier Application
Items
38
Size
12.1 KB
AWSTemplateFormatVersion: '2010-09-09'
Description: ''
Resources:
Vpc:
Type: 'AWS::EC2::VPC'
Properties:
CidrBlock: 10.0.0.0/16
EnableDnsHostnames: true
EnableDnsSupport: true
InstanceTenancy: default
VpcSubnet0:
Type: 'AWS::EC2::Subnet'
Properties:
CidrBlock: 10.0.0.0/24
MapPublicIpOnLaunch: true
VpcId:
Ref: Vpc
AvailabilityZone:
'Fn::Select':
- '0'
- 'Fn::GetAZs':
Ref: 'AWS::Region'
Tags:
- Key: Name
Value: public-az1
VpcSubnet1:
Type: 'AWS::EC2::Subnet'
Properties:
CidrBlock: 10.0.1.0/24
MapPublicIpOnLaunch: true
VpcId:
Ref: Vpc
AvailabilityZone:
'Fn::Select':
- '1'
- 'Fn::GetAZs':
Ref: 'AWS::Region'
Tags:
- Key: Name
Value: public-az2
VpcSubnet2:
Type: 'AWS::EC2::Subnet'
Properties:
CidrBlock: 10.0.2.0/24
MapPublicIpOnLaunch: true
VpcId:
Ref: Vpc
AvailabilityZone:
'Fn::Select':
- '2'
- 'Fn::GetAZs':
Ref: 'AWS::Region'
Tags:
- Key: Name
Value: public-az3
VpcSubnet3:
Type: 'AWS::EC2::Subnet'
Properties:
CidrBlock: 10.0.10.0/24
MapPublicIpOnLaunch: false
VpcId:
Ref: Vpc
AvailabilityZone:
'Fn::Select':
- '0'
- 'Fn::GetAZs':
Ref: 'AWS::Region'
Tags:
- Key: Name
Value: private-az1
VpcSubnet4:
Type: 'AWS::EC2::Subnet'
Properties:
CidrBlock: 10.0.11.0/24
MapPublicIpOnLaunch: false
VpcId:
Ref: Vpc
AvailabilityZone:
'Fn::Select':
- '1'
- 'Fn::GetAZs':
Ref: 'AWS::Region'
Tags:
- Key: Name
Value: private-az2
VpcSubnet5:
Type: 'AWS::EC2::Subnet'
Properties:
CidrBlock: 10.0.12.0/24
MapPublicIpOnLaunch: false
VpcId:
Ref: Vpc
AvailabilityZone:
'Fn::Select':
- '2'
- 'Fn::GetAZs':
Ref: 'AWS::Region'
Tags:
- Key: Name
Value: private-az3
VpcSubnet6:
Type: 'AWS::EC2::Subnet'
Properties:
CidrBlock: 10.0.20.0/24
MapPublicIpOnLaunch: false
VpcId:
Ref: Vpc
AvailabilityZone:
'Fn::Select':
- '0'
- 'Fn::GetAZs':
Ref: 'AWS::Region'
Tags:
- Key: Name
Value: protected-az1
VpcSubnet7:
Type: 'AWS::EC2::Subnet'
Properties:
CidrBlock: 10.0.21.0/24
MapPublicIpOnLaunch: false
VpcId:
Ref: Vpc
AvailabilityZone:
'Fn::Select':
- '1'
- 'Fn::GetAZs':
Ref: 'AWS::Region'
Tags:
- Key: Name
Value: protected-az2
VpcSubnet8:
Type: 'AWS::EC2::Subnet'
Properties:
CidrBlock: 10.0.22.0/24
MapPublicIpOnLaunch: false
VpcId:
Ref: Vpc
AvailabilityZone:
'Fn::Select':
- '2'
- 'Fn::GetAZs':
Ref: 'AWS::Region'
Tags:
- Key: Name
Value: protected-az3
VpcIgw:
Type: 'AWS::EC2::InternetGateway'
Properties: {}
VpcIgwAttachment:
Type: 'AWS::EC2::VPCGatewayAttachment'
Properties:
InternetGatewayId:
Ref: VpcIgw
VpcId:
Ref: Vpc
VpcEipNatGw0:
Type: 'AWS::EC2::EIP'
Properties:
Domain: vpc
VpcNatGw0:
Type: 'AWS::EC2::NatGateway'
Properties:
SubnetId:
Ref: VpcSubnet0
ConnectivityType: public
AllocationId:
'Fn::GetAtt':
- VpcEipNatGw0
- AllocationId
VpcRouteTable0:
Type: 'AWS::EC2::RouteTable'
Properties:
VpcId:
Ref: Vpc
Tags:
- Key: Name
Value: Public Route Table
VpcRouteTable0Assoc0:
Type: 'AWS::EC2::SubnetRouteTableAssociation'
Properties:
RouteTableId:
Ref: VpcRouteTable0
SubnetId:
Ref: VpcSubnet0
VpcRouteTable0Assoc1:
Type: 'AWS::EC2::SubnetRouteTableAssociation'
Properties:
RouteTableId:
Ref: VpcRouteTable0
SubnetId:
Ref: VpcSubnet1
VpcRouteTable0Assoc2:
Type: 'AWS::EC2::SubnetRouteTableAssociation'
Properties:
RouteTableId:
Ref: VpcRouteTable0
SubnetId:
Ref: VpcSubnet2
VpcRouteTable0VpcRoute0:
Type: 'AWS::EC2::Route'
Properties:
DestinationCidrBlock: 0.0.0.0/0
RouteTableId:
Ref: VpcRouteTable0
GatewayId:
Ref: VpcIgw
VpcRouteTable1:
Type: 'AWS::EC2::RouteTable'
Properties:
VpcId:
Ref: Vpc
Tags:
- Key: Name
Value: Private Route Table
VpcRouteTable1Assoc3:
Type: 'AWS::EC2::SubnetRouteTableAssociation'
Properties:
RouteTableId:
Ref: VpcRouteTable1
SubnetId:
Ref: VpcSubnet3
VpcRouteTable1Assoc4:
Type: 'AWS::EC2::SubnetRouteTableAssociation'
Properties:
RouteTableId:
Ref: VpcRouteTable1
SubnetId:
Ref: VpcSubnet4
VpcRouteTable1Assoc5:
Type: 'AWS::EC2::SubnetRouteTableAssociation'
Properties:
RouteTableId:
Ref: VpcRouteTable1
SubnetId:
Ref: VpcSubnet5
VpcRouteTable1VpcRoute0:
Type: 'AWS::EC2::Route'
Properties:
DestinationCidrBlock: 0.0.0.0/0
RouteTableId:
Ref: VpcRouteTable1
NatGatewayId:
Ref: VpcNatGw0
VpcRouteTable2:
Type: 'AWS::EC2::RouteTable'
Properties:
VpcId:
Ref: Vpc
Tags:
- Key: Name
Value: Protected Route Table
VpcRouteTable2Assoc6:
Type: 'AWS::EC2::SubnetRouteTableAssociation'
Properties:
RouteTableId:
Ref: VpcRouteTable2
SubnetId:
Ref: VpcSubnet6
VpcRouteTable2Assoc7:
Type: 'AWS::EC2::SubnetRouteTableAssociation'
Properties:
RouteTableId:
Ref: VpcRouteTable2
SubnetId:
Ref: VpcSubnet7
VpcRouteTable2Assoc8:
Type: 'AWS::EC2::SubnetRouteTableAssociation'
Properties:
RouteTableId:
Ref: VpcRouteTable2
SubnetId:
Ref: VpcSubnet8
Ec2LaunchTemplate:
Type: 'AWS::EC2::LaunchTemplate'
Properties:
LaunchTemplateData:
ImageId:
Ref: amazon2
DisableApiTermination: false
InstanceInitiatedShutdownBehavior: stop
Monitoring:
Enabled: false
MetadataOptions:
HttpEndpoint: enabled
HttpTokens: required
NetworkInterfaces:
- DeleteOnTermination: true
DeviceIndex: 0
SubnetId:
Ref: VpcSubnet3
Groups:
- 'Fn::GetAtt':
- ApplicationSecurityGroup
- GroupId
AutoScalingGroup:
Type: 'AWS::AutoScaling::AutoScalingGroup'
Properties:
MinSize: '1'
MaxSize: '1'
DesiredCapacity: '1'
HealthCheckType: EC2
LaunchTemplate:
LaunchTemplateId:
Ref: Ec2LaunchTemplate
Version:
'Fn::GetAtt':
- Ec2LaunchTemplate
- LatestVersionNumber
VPCZoneIdentifier:
- Ref: VpcSubnet3
- Ref: VpcSubnet4
- Ref: VpcSubnet5
TargetGroupARNs:
- Ref: ApplicationLoadBalancerTargetGroup1
ApplicationSecurityGroup:
Type: 'AWS::EC2::SecurityGroup'
Properties:
GroupDescription: Security Group for Application EC2 Instances
VpcId:
Ref: Vpc
SecurityGroupEgress:
- FromPort: -1
ToPort: -1
IpProtocol: '-1'
Description: ''
CidrIp: 0.0.0.0/0
SecurityGroupIngress:
- FromPort: 80
ToPort: 80
IpProtocol: tcp
Description: Allow HTTP traffic
SourceSecurityGroupId:
'Fn::GetAtt':
- ApplicationLoadBalancerSecurityGroup
- GroupId
GroupName: application-ec2-sg
ApplicationLoadBalancerSecurityGroup:
Type: 'AWS::EC2::SecurityGroup'
Properties:
GroupDescription: Security Group for Application Load Balancer
VpcId:
Ref: Vpc
SecurityGroupEgress:
- FromPort: -1
ToPort: -1
IpProtocol: '-1'
Description: ''
CidrIp: 0.0.0.0/0
SecurityGroupIngress:
- FromPort: 443
ToPort: 443
IpProtocol: tcp
Description: Allow HTTPS traffic
CidrIp: 0.0.0.0/0
GroupName: alb-sg
RdsSecurityGroup:
Type: 'AWS::EC2::SecurityGroup'
Properties:
GroupDescription: Security Group for RDS
VpcId:
Ref: Vpc
SecurityGroupEgress:
- FromPort: -1
ToPort: -1
IpProtocol: '-1'
Description: ''
CidrIp: 0.0.0.0/0
SecurityGroupIngress:
- FromPort: '5432'
ToPort: '5432'
IpProtocol: tcp
Description: Allow RDS traffic
SourceSecurityGroupId:
'Fn::GetAtt':
- ApplicationSecurityGroup
- GroupId
GroupName: rds-sg
ApplicationLoadBalancer:
Type: 'AWS::ElasticLoadBalancingV2::LoadBalancer'
Properties:
Type: application
Scheme: internet-facing
IpAddressType: ipv4
SecurityGroups:
- 'Fn::GetAtt':
- ApplicationLoadBalancerSecurityGroup
- GroupId
Subnets:
- Ref: VpcSubnet0
- Ref: VpcSubnet1
- Ref: VpcSubnet2
LoadBalancerAttributes:
- Key: deletion_protection.enabled
Value: false
- Key: access_logs.s3.enabled
Value: false
- Key: idle_timeout.timeout_seconds
Value: 60
- Key: routing.http.desync_mitigation_mode
Value: defensive
- Key: routing.http.drop_invalid_header_fields.enabled
Value: false
- Key: routing.http.x_amzn_tls_version_and_cipher_suite.enabled
Value: false
- Key: routing.http.xff_client_port.enabled
Value: false
- Key: routing.http2.enabled
Value: true
- Key: waf.fail_open.enabled
Value: false
ApplicationLoadBalancerTargetGroup1:
Type: 'AWS::ElasticLoadBalancingV2::TargetGroup'
Properties:
TargetType: instance
VpcId:
Ref: Vpc
Protocol: HTTP
ProtocolVersion: HTTP1
Port: 80
HealthCheckEnabled: true
HealthCheckPath: /
HealthCheckIntervalSeconds: 30
HealthCheckProtocol: HTTP
HealthCheckPort: 80
HealthCheckTimeoutSeconds: 5
HealthyThresholdCount: 5
UnhealthyThresholdCount: 2
Matcher:
HttpCode: '200'
ApplicationLoadBalancerListener1:
Type: 'AWS::ElasticLoadBalancingV2::Listener'
Properties:
LoadBalancerArn:
Ref: ApplicationLoadBalancer
Protocol: HTTPS
Port: 443
DefaultActions:
- Type: forward
ForwardConfig:
TargetGroups:
- TargetGroupArn:
Ref: ApplicationLoadBalancerTargetGroup1
Certificates:
- CertificateArn: ''
SslPolicy: ELBSecurityPolicy-2016-08
RdsDBSubnetGroup:
Type: 'AWS::RDS::DBSubnetGroup'
Properties:
DBSubnetGroupName: mydbsubnetgroup
DBSubnetGroupDescription: Subnet Group for three tier application database
SubnetIds:
- Ref: VpcSubnet6
- Ref: VpcSubnet7
- Ref: VpcSubnet8
RdsInstance:
Type: 'AWS::RDS::DBInstance'
Properties:
DBInstanceClass: db.t3.medium
MultiAZ: false
Engine: postgres
EngineVersion: '13.4'
DBSubnetGroupName:
Ref: RdsDBSubnetGroup
MasterUsername: dbadmin
MasterUserPassword:
'Fn::Sub': '{{resolve:secretsmanager:${DbSecret}}}'
Port: '5432'
DBInstanceIdentifier: rds-postgres
AllocatedStorage: '50'
StorageEncrypted: false
StorageType: standard
BackupRetentionPeriod: 1
DeleteAutomatedBackups: true
DeletionProtection: false
VPCSecurityGroups:
- 'Fn::GetAtt':
- RdsSecurityGroup
- GroupId
Parameters:
amazon2:
Type: 'AWS::SSM::Parameter::Value<AWS::EC2::Image::Id>'
Default: /aws/service/ami-amazon-linux-latest/amzn2-ami-hvm-x86_64-gp2
Metadata: {}
Conditions: {}
