You must be logged in to view saved presets
Guided Walkthroughs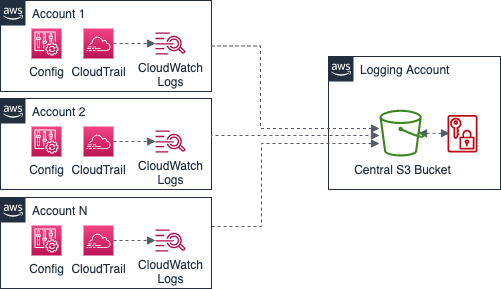
Security Logging/Monitoring Services
Dedicated Logging Account (CloudTrail & Config)

Overview
- This guide configures CloudTrail and Config in a multi-account environment and provides the necessary templates for:
- Configure the central logging account with the necessary S3 and KMS resources to store the logs centrally with KMS encryption
- Configure other member AWS accounts to enable AWS CloudTrail and/or AWS Config and forward the logs to the central logging account
- This guide provides the option to use CloudFormation StackSets to deploy the member account configuration to multiple AWS accounts at once (and optionally future accounts in an organization).
- Important: This guide requires a recent scan of your organization management AWS account to ensure an up-to-date view of the AWS environment, configuration, and resources
A premium subscription is required for this content
Configuration
Deploy
Logging Account Configuration (S3 Buckets)
Items
3
Size
2.6 KB
AWSTemplateFormatVersion: '2010-09-09'
Description: ''
Resources:
LogEncryptionKey:
Type: 'AWS::KMS::Key'
Properties:
EnableKeyRotation: true
MultiRegion: false
Description: KMS encryption key for CloudTrail logs
KeyPolicy:
Version: '2012-10-17'
Statement:
- Sid: Enable IAM User Permissions
Effect: Allow
Principal:
AWS:
'Fn::Join':
- ''
- - 'arn:aws:iam::'
- Ref: 'AWS::AccountId'
- ':root'
Action: 'kms:*'
Resource: '*'
- Sid: Enable CloudTrail Permissions
Effect: Allow
Principal:
Service: cloudtrail.amazonaws.com
Action:
- 'kms:DescribeKey'
- 'kms:Decrypt'
- 'kms:GenerateDataKey*'
Resource: '*'
SharedLoggingBucket:
Type: 'AWS::S3::Bucket'
Properties:
BucketEncryption:
ServerSideEncryptionConfiguration:
- BucketKeyEnabled: false
ServerSideEncryptionByDefault:
SSEAlgorithm: 'aws:kms'
KMSMasterKeyID:
Ref: LogEncryptionKey
VersioningConfiguration:
Status: Suspended
PublicAccessBlockConfiguration:
BlockPublicAcls: true
BlockPublicPolicy: true
IgnorePublicAcls: true
RestrictPublicBuckets: true
BucketPolicy:
Type: 'AWS::S3::BucketPolicy'
Properties:
Bucket:
Ref: SharedLoggingBucket
PolicyDocument:
Version: '2012-10-17'
Statement:
- Principal:
Service:
- cloudtrail.amazonaws.com
- config.amazonaws.com
Action:
- 's3:GetBucketAcl'
Resource:
- 'Fn::GetAtt':
- SharedLoggingBucket
- Arn
Effect: Allow
Condition: {}
- Principal:
Service:
- cloudtrail.amazonaws.com
- config.amazonaws.com
Action:
- 's3:PutObject'
Resource:
- 'Fn::Join':
- ''
- - ''
- 'Fn::GetAtt':
- SharedLoggingBucket
- Arn
- /*
Effect: Allow
Condition:
StringEquals:
's3:x-amz-acl': bucket-owner-full-control
DependsOn: SharedLoggingBucket
Parameters: {}
Metadata: {}
Conditions: {}
Security Logging/Monitoring Services
Items
4
Size
1.7 KB
AWSTemplateFormatVersion: '2010-09-09'
Description: ''
Resources:
CloudTrail:
Type: 'AWS::CloudTrail::Trail'
Properties:
TrailName: ManagementEventsTrail
IsLogging: true
EnableLogFileValidation: true
EventSelectors:
- IncludeManagementEvents: true
ReadWriteType: All
IsMultiRegionTrail: true
IncludeGlobalServiceEvents: true
S3BucketName: ''
ConfigurationRecorder:
Type: 'AWS::Config::ConfigurationRecorder'
Properties:
RoleARN:
'Fn::GetAtt':
- IamRoleForAwsConfig
- Arn
RecordingGroup:
AllSupported: true
IncludeGlobalResourceTypes: true
DeliveryChannel:
Type: 'AWS::Config::DeliveryChannel'
Properties:
S3BucketName: ''
IamRoleForAwsConfig:
Type: 'AWS::IAM::Role'
Properties:
ManagedPolicyArns:
- 'arn:aws:iam::aws:policy/service-role/AWS_ConfigRole'
AssumeRolePolicyDocument:
Version: '2012-10-17'
Statement:
- Sid: ''
Effect: Allow
Principal:
Service: config.amazonaws.com
Action: 'sts:AssumeRole'
Policies:
- PolicyName: allow-access-to-config-s3-bucket
PolicyDocument:
Version: '2012-10-17'
Statement:
- Effect: Allow
Action:
- 's3:PutObject'
Resource:
- 'arn:aws:s3:::/*'
Condition:
StringLike:
's3:x-amz-acl': bucket-owner-full-control
- Effect: Allow
Action:
- 's3:GetBucketAcl'
Resource: 'arn:aws:s3:::'
Parameters: {}
Metadata: {}
Conditions: {}
